October 21, 2025
CJIS Compliance for Grants: Common Questions Answered
Managing federal public safety grants requires strict CJIS compliance. Without it, agencies risk losing funding and facing operational challenges. Here's what you need to know:
- CJIS compliance is mandatory for any project involving federal IT funds, ensuring the protection of sensitive criminal justice information (CJI).
- Agencies must adhere to the CJIS Security Policy, covering technical and administrative safeguards across all government levels.
- Key challenges include managing third-party access, ensuring accurate reporting, and navigating multi-jurisdictional compliance.
Grantwell simplifies this process by integrating compliance tools into grant management, from access controls to automated reporting. Staying compliant means protecting data, meeting funding requirements, and avoiding penalties.
Improve your Security Policy with FBI CJIS
CJIS Requirements for Grant-Funded Projects
When federal public safety grants are involved, following the CJIS Security Policy isn’t optional - it’s mandatory. This policy outlines key technical and administrative measures to safeguard criminal justice data at every stage of a grant-funded project. Understanding these requirements early on is crucial for ensuring sensitive data stays protected. Compliance isn’t limited to one level of government; it’s a shared responsibility across federal, state, and local agencies.
Compliance Responsibilities at Federal, State, and Local Levels
At the federal level, oversight ensures that grant-funded projects align with CJIS standards. State and local agencies take on the task of implementing and managing these controls. For projects involving multiple jurisdictions, coordinated protocols are essential to ensure all parties meet the required security measures.
How Grantwell Simplifies CJIS Compliance
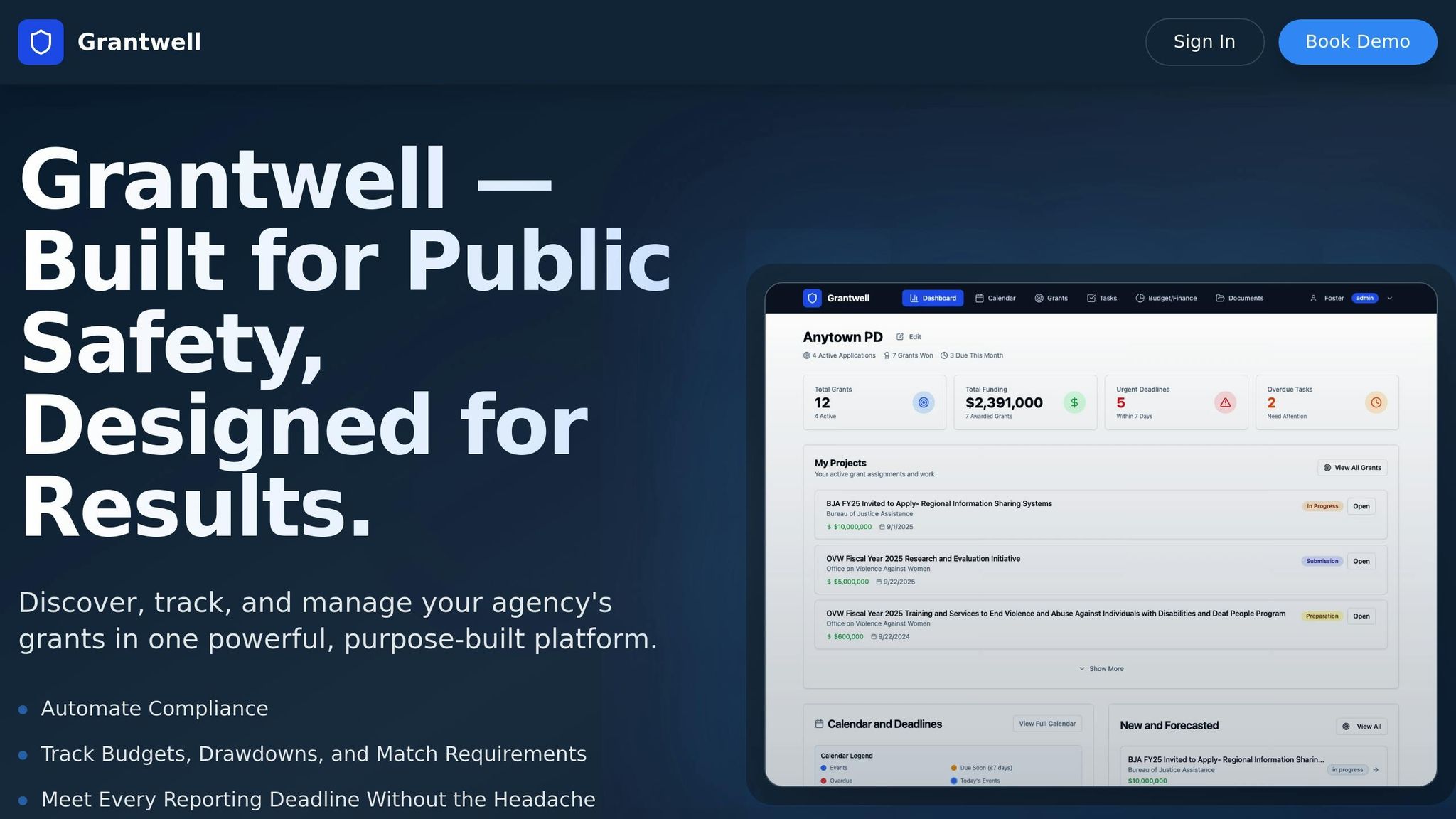
Navigating CJIS compliance can be tricky, with its intricate rules and overlapping jurisdictional requirements. Grantwell makes this process easier by integrating compliance measures directly into every stage of grant management, streamlining the entire experience.
sbb-itb-6e14cfc
Best Practices for Maintaining CJIS Compliance
Staying compliant with CJIS standards requires ongoing attention and a well-organized, audit-ready documentation process. Agencies must adopt structured practices that ensure their records meet CJIS requirements and are always prepared for review. At the heart of this effort are two key elements: clear documentation and audit readiness.
Documentation and Audit Preparation
When preparing documentation, it’s crucial to keep CJIS audits and compliance reviews in mind. Each state or territory has a CJIS Systems Agency (CSA) and designated Criminal Justice Information Services Officers (CSOs) responsible for enforcing compliance protocols[1]. Your documentation should align closely with the guidelines set by these authorities.
The FBI's CJIS Advisory Process plays a significant role in compliance oversight. Its Compliance Evaluation Subcommittee reviews audits and enforces sanctions against agencies that fail to meet standards[1]. This highlights why meticulous preparation and adherence to CJIS protocols are non-negotiable for maintaining compliance.
Common CJIS Compliance Challenges and Solutions
Navigating CJIS compliance can be tricky, especially when agencies face unique challenges tied to grant-funded projects. Tackling these obstacles head-on is essential to avoid costly setbacks and maintain operational security. Below, we’ll dive into some of the most common hurdles and practical solutions to keep agencies on track.
Managing Third-Party and Contractor Access
One of the biggest compliance risks arises when external contractors, consultants, or vendors need access to sensitive criminal justice information (CJI). To meet CJIS standards, every individual accessing CJI - whether they’re part of a subcontractor team or working across multiple jurisdictions - must pass background checks and complete required training. The responsibility for ensuring compliance ultimately falls on the agency, even when vendors are involved.
Grantwell offers a role-based access control (RBAC) system that simplifies this process. Administrators can assign specific permission levels tailored to CJIS security requirements, ensuring contractors only access the data they need for their role. The system also maintains detailed audit trails, tracking who accessed what and when, which is crucial for compliance reporting.
To further enhance security, Grantwell includes automated access reviews. These periodic prompts ensure that administrators regularly review and update permissions, reducing the risk of former contractors or inactive users retaining access to sensitive information.
Ensuring Timely and Accurate Reporting
Accurate and timely reporting is another major challenge for CJIS-compliant agencies, especially when federal grant deadlines loom. Manual data handling increases the likelihood of errors, missed deadlines, or even compliance violations if sensitive information is mishandled.
Grantwell’s automated workflow system addresses these issues by centralizing grant data and generating reports that meet CJIS and Department of Justice standards. The platform’s JustGrants-compatible reporting tools eliminate the need for manual data entry, reducing errors and streamlining the submission process.
The system also keeps tabs on grant milestones, budgets, and performance metrics in real time. This means administrators can generate accurate reports at any stage of the grant lifecycle, whether for mid-term reviews or urgent federal inquiries.
Managing Multi-Jurisdictional Compliance
Regional or multi-state grant projects come with a unique set of challenges. Different jurisdictions may interpret CJIS guidelines in varying ways or impose additional local requirements, making compliance a moving target. When multiple agencies or states are involved, ensuring a consistent approach that meets the strictest standards can be daunting.
Grantwell’s centralized compliance tracking tools simplify this process by creating separate compliance profiles for each jurisdiction while providing a consolidated dashboard. This setup allows administrators to monitor overall compliance at a glance and quickly address potential issues.
The platform also features automated compliance monitoring, which continuously checks project activities against the requirements of all involved jurisdictions. If any action risks violating local regulations, administrators receive alerts, allowing them to resolve issues before they escalate.
To further ease the burden, Grantwell’s standardized reporting framework generates jurisdiction-specific reports while maintaining uniform data collection and analysis methods. This ensures every participating agency gets the documentation they need in their preferred format, without creating extra work for administrators.
Achieving CJIS Compliance with Grantwell
Grantwell simplifies the intricate process of managing CJIS compliance for federal grants by tackling the challenges head-on. This AI-powered platform, built on a FedRAMP-aligned framework, is tailored specifically for municipalities and public safety agencies. From the initial grant application to the final closeout, Grantwell integrates essential compliance functions into a single, streamlined system.
By bringing together budgeting, reporting, and financial oversight in one platform, Grantwell enhances transparency while reducing the need for manual intervention. This approach helps agencies meet federal audit and security standards with greater efficiency. It also directly addresses issues like multi-jurisdictional coordination and third-party access, which are often hurdles in maintaining CJIS compliance.
Since CJIS compliance requirements can differ across agencies, it’s crucial for each organization to assess its specific needs. Grantwell serves as a powerful tool within a broader strategy to ensure adherence to all necessary security protocols.
FAQs
What are the main requirements of the CJIS Security Policy for agencies managing federal public safety grants?
The CJIS Security Policy sets essential guidelines to protect Criminal Justice Information (CJI) at every stage - whether it’s being created, accessed, shared, stored, or disposed of. These rules align with federal laws, FBI regulations, and the standards of the criminal justice community.
For agencies managing federal public safety grants, compliance with these protocols is non-negotiable. This includes implementing strict access controls, encrypting sensitive data, and conducting regular audits. These measures apply to every individual and system involved with CJI, ensuring that security and data integrity are maintained throughout projects funded by these grants.
How does Grantwell's role-based access control system ensure secure third-party access to sensitive criminal justice information?
Grantwell’s role-based access control system is designed to ensure that only the right people - whether internal team members or third-party personnel - can access the specific criminal justice information (CJI) they need to perform their duties. By assigning roles with carefully defined permissions, the system reduces the risk of unauthorized access while staying aligned with CJIS standards.
This method not only keeps sensitive data secure but also streamlines how access rights are managed. Grant administrators can more easily monitor and audit user activity, offering an added layer of oversight. With these measures in place, Grantwell helps safeguard public safety initiatives while maintaining compliance.
How can agencies prepare for CJIS audits and stay compliant?
To get ready for CJIS audits and stay compliant, agencies need to prioritize a few key actions. First, make sure every staff member with access to Criminal Justice Information (CJI) is properly trained on the CJIS Security Policy. This training should cover critical topics like encryption, access controls, and secure data handling practices. It's also important to appoint a CJIS Security Officer (CSO) who will oversee compliance efforts and serve as the main point of contact for all related matters.
On the technical side, agencies should implement strong safeguards. This includes encrypting CJI both during transmission and while stored, enforcing strict access controls, and consistently updating security protocols to match policy changes. Keeping detailed logs and documentation is equally important to prove compliance during audits. Lastly, conducting regular internal audits can help identify and address vulnerabilities before any formal review takes place.